In Code Injection vulnerability allows an attacker to inject and execute malicious code on the target web application. This type of attack exploits the poor handling of user-supplied untrusted data. The code injection vulnerability exists on the web-application due to lack of proper validation and security checks against input data (user-supplied data).
The code injection is different from command injection, because in code injection an attacker is only limited by the functionality of the injected language itself. For example, if an attacker is able to inject PHP code into an application and have it executed, he is only limited by what PHP is capable of. Now lets see an example of code injection Vulnerability.
File : test.php
Above code takes input from GET parameter 'name' and evaluate it with echo command by using eval() function, the eval() function is a inbuilt php function which evaluates a string as PHP code. Output of above program :
But the above code is vulnerable to php code injection. For example, an attacker could make the following request to execute arbitrary PHP code.
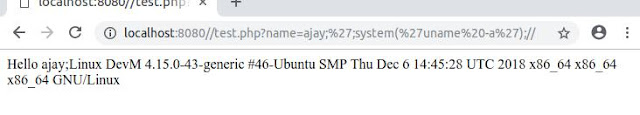
And as we can see, the phpinfo() function is executed by simply commenting out the rest of the code (by using '//' ) on eval() function at line 3. Another example of evaluating system commands :
Avoiding Code Injection Vulnerability :
The best way to eliminate the code injection vulnerability is to avoid code evaluation at all costs. And when it is necessary then it is important to strongly validate the input data before evaluating it.
Visit the link for more tutorials about Web Security : http://www.sec-art.net/p/web-security.html
The code injection is different from command injection, because in code injection an attacker is only limited by the functionality of the injected language itself. For example, if an attacker is able to inject PHP code into an application and have it executed, he is only limited by what PHP is capable of. Now lets see an example of code injection Vulnerability.
File : test.php
<?php
$name = $_GET['name'];
eval("echo 'Hello $name';");
?>
Above code takes input from GET parameter 'name' and evaluate it with echo command by using eval() function, the eval() function is a inbuilt php function which evaluates a string as PHP code. Output of above program :
But the above code is vulnerable to php code injection. For example, an attacker could make the following request to execute arbitrary PHP code.
/test.php?name=ajay;';phpinfo();//And as we can see, the phpinfo() function is executed by simply commenting out the rest of the code (by using '//' ) on eval() function at line 3. Another example of evaluating system commands :
/test.php?name=ajay;';system('uname -a');//Avoiding Code Injection Vulnerability :
The best way to eliminate the code injection vulnerability is to avoid code evaluation at all costs. And when it is necessary then it is important to strongly validate the input data before evaluating it.
Visit the link for more tutorials about Web Security : http://www.sec-art.net/p/web-security.html